Anticipate-Affect
Scientists are developing sophisticated modeling and research techniques to give them an advantage in their ability to anticipate and affect explosive-related threats or events.

Sophisticated modeling and research techniques to counter threats
What conditions lead an individual or group toward committing political violence? Is it possible to accurately forecast who will become radicalized or even estimate when they might resort to violence?
These and similar questions weigh heavily on the minds of security specialists and decision makers around the world. At Los Alamos, scientists are developing sophisticated modeling and research techniques to give them an advantage in their ability to anticipate and affect explosive-related threats or events. The idea is to help counter such threats before anything actually happens.
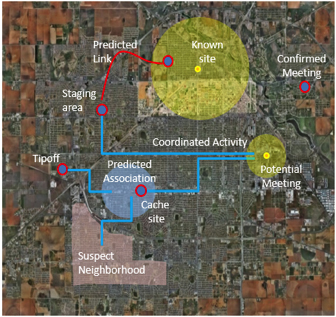
Agent-based modeling simulates complex social systems made up of interacting “agents,” either individuals or groups. Scientists gather information on how people or groups have behaved over time and encode that information into the model’s algorithms, then performs simulations to see the patterns of system behavior that might play out under possible future situations.
Modeling techniques incorporate socio-cultural data to understand what influences, characterizes, and enables human networks to carry out asymmetric acts. Further data mining enables Los Alamos scientists to collect and analyze data regarding social and cultural behavior. Los Alamos also plays a large role in training members of the military in explosive threat response.
The facilities and experienced personnel at Los Alamos provide a perfect environment for such essential training programs. Anticipate capabilities provide knowledge and models that enable US forces to anticipate and affect explosive threats or events. Such capabilities include the following:
- Conducting socio-cultural modeling to better understand and identify what influences, characterizes, and enables human networks to carry out asymmetric acts
- Data mining and analytics to collect and evaluate social and cultural behavior
- Executing persistent surveillance
- Training in improvised explosive threats


